AWS PrivateLink
AWS PrivateLink is an AWS service which allows one-way secure access to Rockset from a customer's VPC without API requests or queries ever traversing through the public internet. It provides additional security and protection against data exfiltration and allows customers to take advantage of Rockset's fully managed real-time analytics platform while meeting high security standards.
Architecture
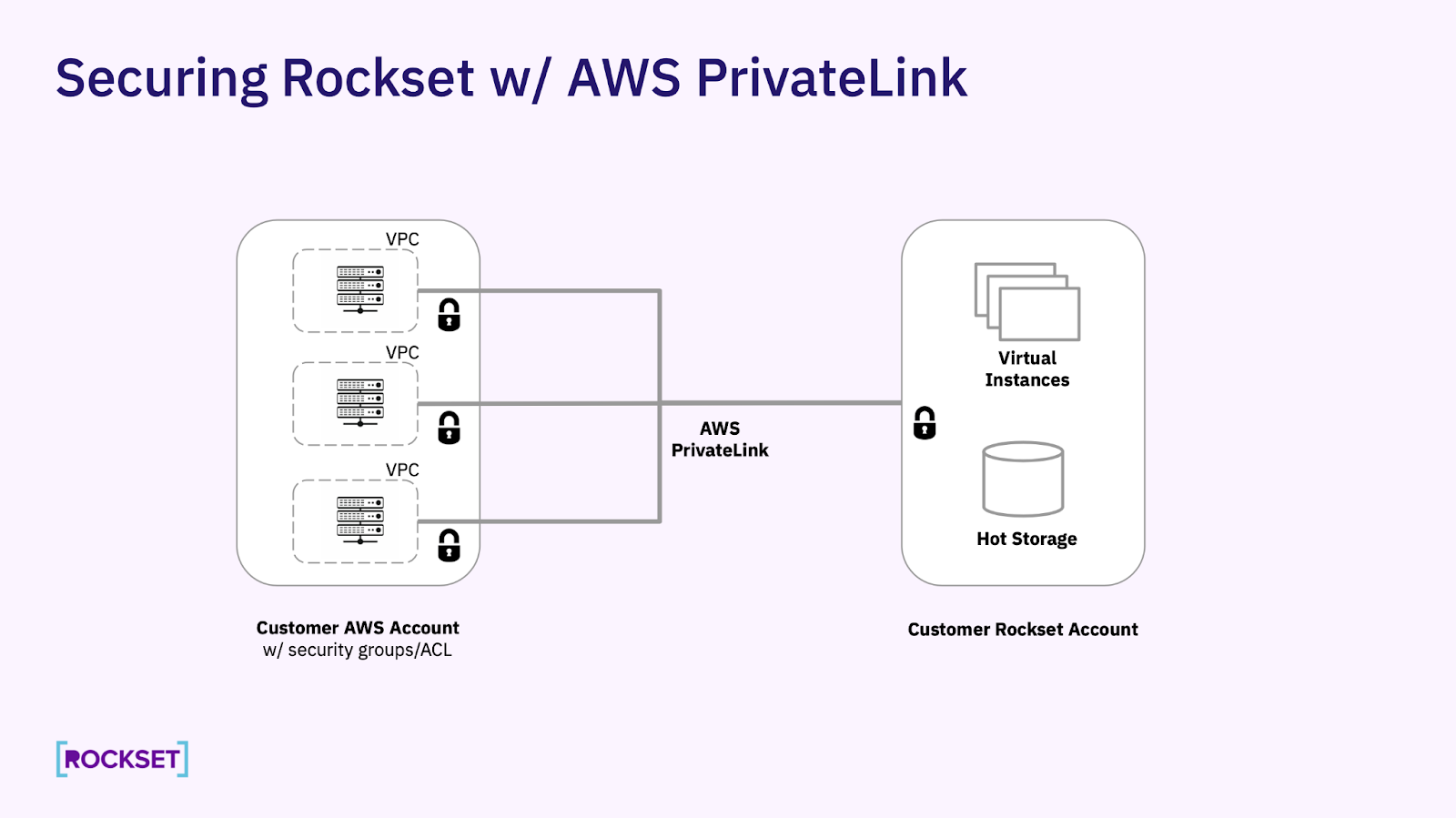
- All traffic that flows through the AWS PrivateLink will incur additional network expenses in your AWS account. Please work with your Rockset and AWS solutions partners to estimate what those charges would be ahead of time to avoid surprises. These AWS network charges will be accrued for every AZ in every VPC endpoint ($/hour) from which you will be accessing Rockset in addition to the network transfer costs based on data transferred over the AWS PrivateLink ($/GiB).
- Use IP Allowlisting to allow IP addresses from which administrators might want to access their Rockset account. This will help administrators troubleshoot issues without the fear of getting locked out of their Rockset account.
- You will need outbound Internet access to access and login to the Rockset Console. This is required for the Rockset Console to authenticate the user including enforcing SSO and Multi-Factor Authentication. Once authenticated, all console traffic will traverse through AWS PrivateLink. This requirement only applies for accessing Rockset Console. Applications can connect securely to Rockset using API keys over the AWS PrivateLink API endpoint and your servers hosting your application do not need outbound Internet access.
Installation
API endpoint addresses will vary by region.
The following set of instructions uses the Frankfurt region as an example.
Step 1: Register your AWS Account with Rockset
Please provide your 12 digit AWS account ID to your Rockset solutions architect.
Step 2: Configure your AWS VPC endpoint
In your AWS account, create a VPC endpoint by following directions on the AWS docs.
- Go to "Create Endpoint".
- Create an endpoint and select "Other endpoint services".
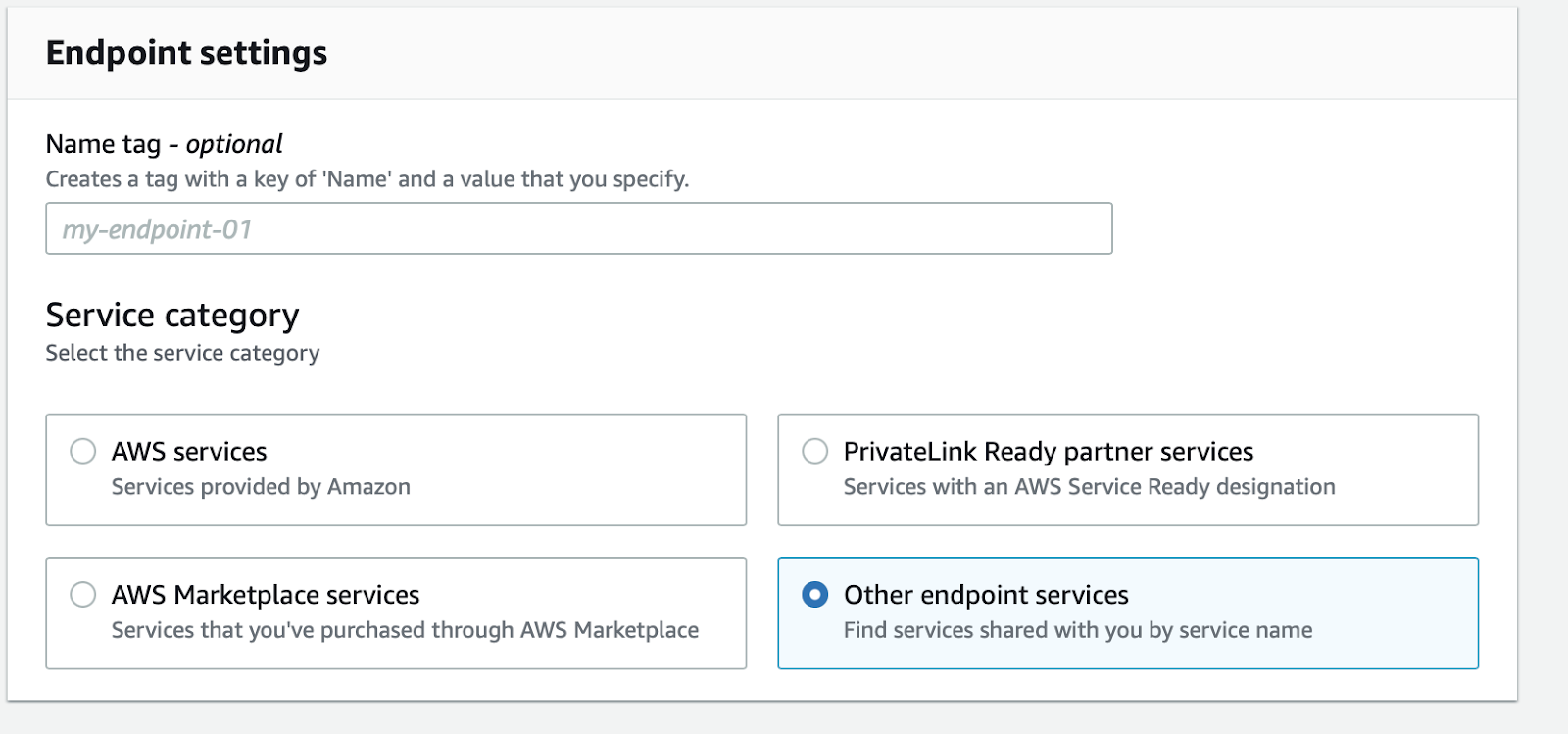
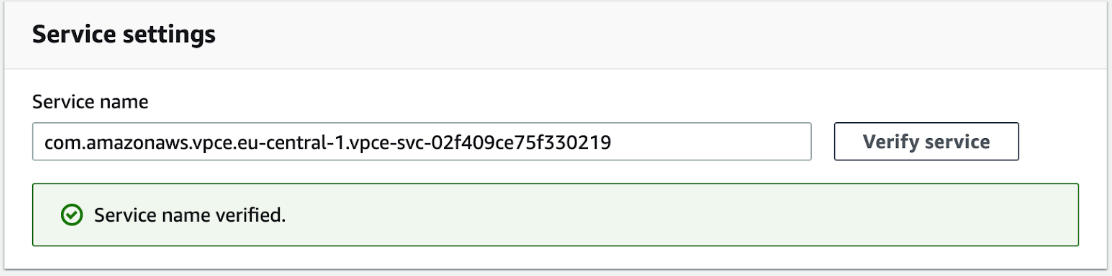
- Set the correct VPC endpoint service depending on region.
- Use
com.amazonaws.vpce.eu-central-1.vpce-svc-02f409ce75f330219for Frankfurt. - Use
com.amazonaws.vpce.us-west-2.vpce-svc-030e98de8dbf451c0for Oregon. - Use
com.amazonaws.vpce.us-east-1.vpce-svc-00b38ed8b65eac319for N. Virginia. - Use
com.amazonaws.vpce.ap-southeast-2.vpce-svc-0e87c1c5e53c17630for Sydney. - Use
com.amazonaws.vpce.eu-west-1.vpce-svc-0a6d7db7c0b18f762for Dublin.
- Use
- Choose the VPC you want to use to connect to the endpoint
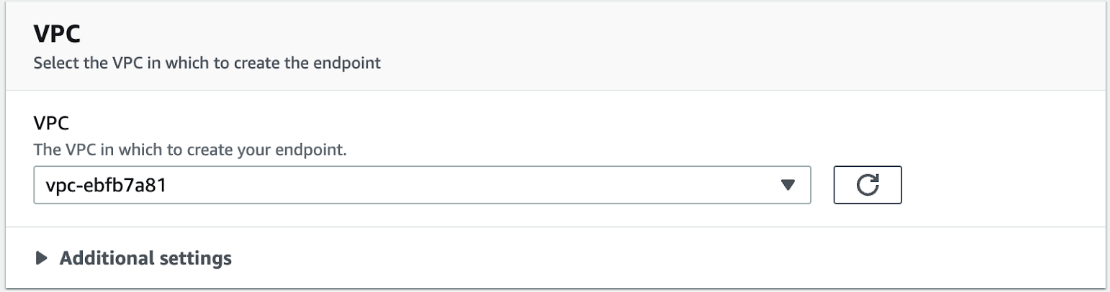
- Next, expand "Additional Settings" and check "Enable DNS name". Refer to the info blurb to ensure you have the correct VPC attributes enabled.
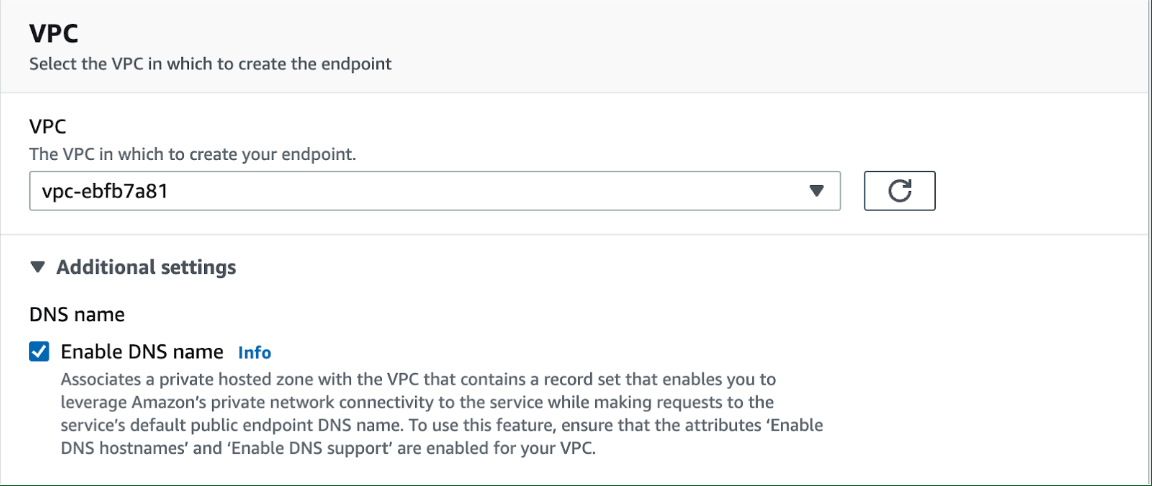
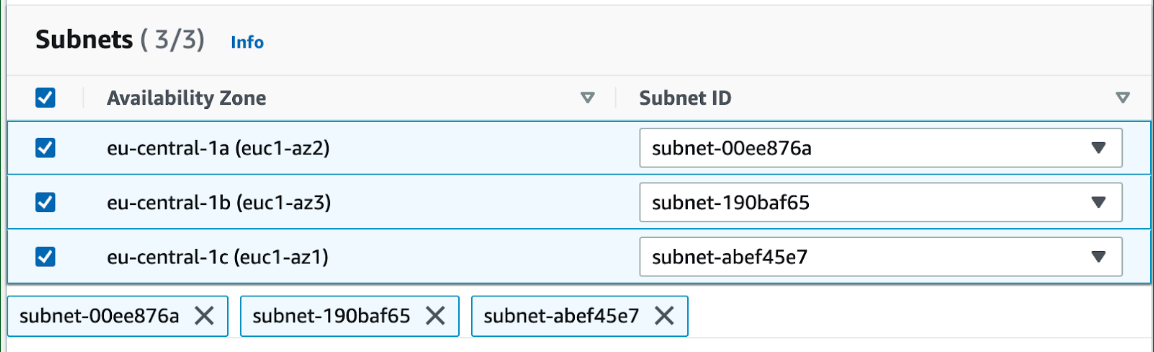
- Once you select VPC, you can set your subnets for your availability zones. These are subnets where the resources that connect to privatelink live. Our load balancers may not be present in every availability zone in the region, but as long as you can route through the subnets capable of connecting to privatelink, you should not experience any issues. Contact our support team if this does not work for you.
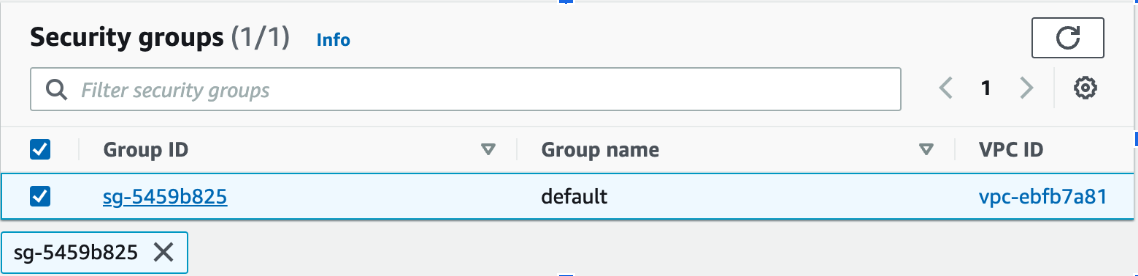
- Set a security group. Note that this security group must allow port 443 inbound from wherever your requests originate, as that is the port required to make API requests to Rockset.
- Hit create endpoint
Wait for the endpoint to go from “Pending” to “Active”. This usually takes about 5 minutes.
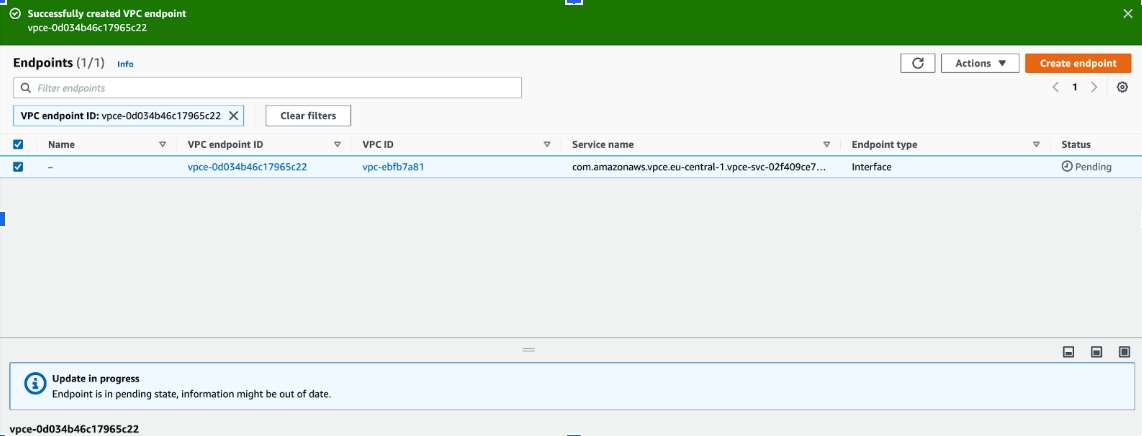
- Verify that the "Private DNS names enabled" section reads "Yes"
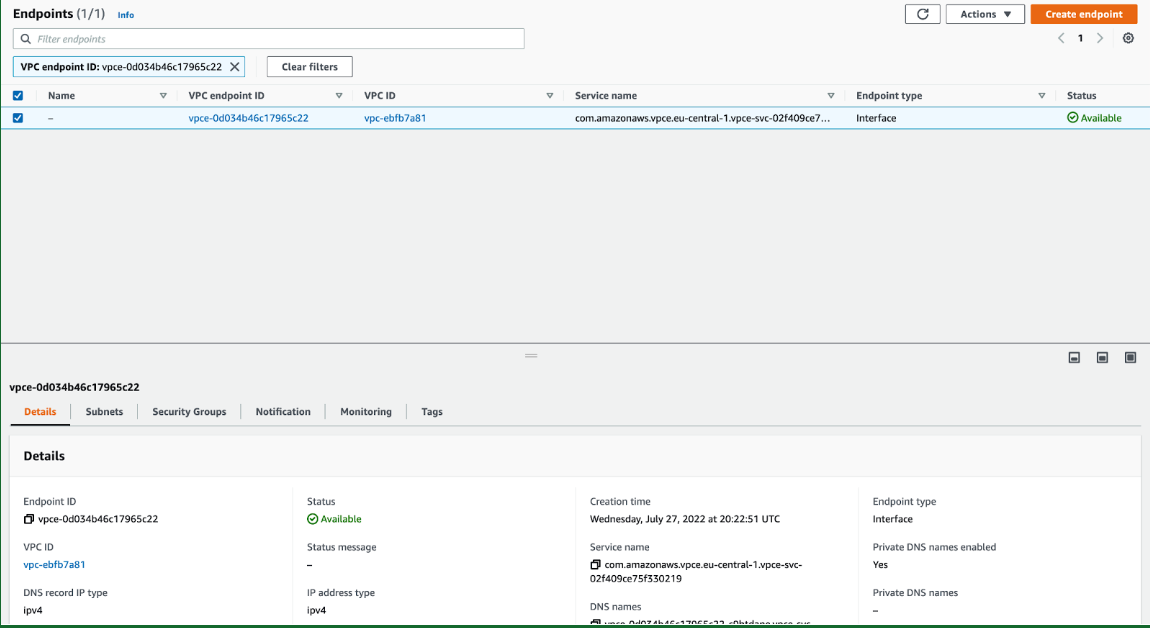
At this point your Rockset account can be accessed both via the AWS PrivateLink API endpoint and the public API endpoint (example for Frankfurt region: api.euc1a1.rockset.com). Follow steps below to turn off your public API endpoint.
Step 3: Validate connectivity
If the steps above were set up correctly, then at this point you should be able to access Rockset from both the AWS PrivateLink API endpoint and the public API endpoint.
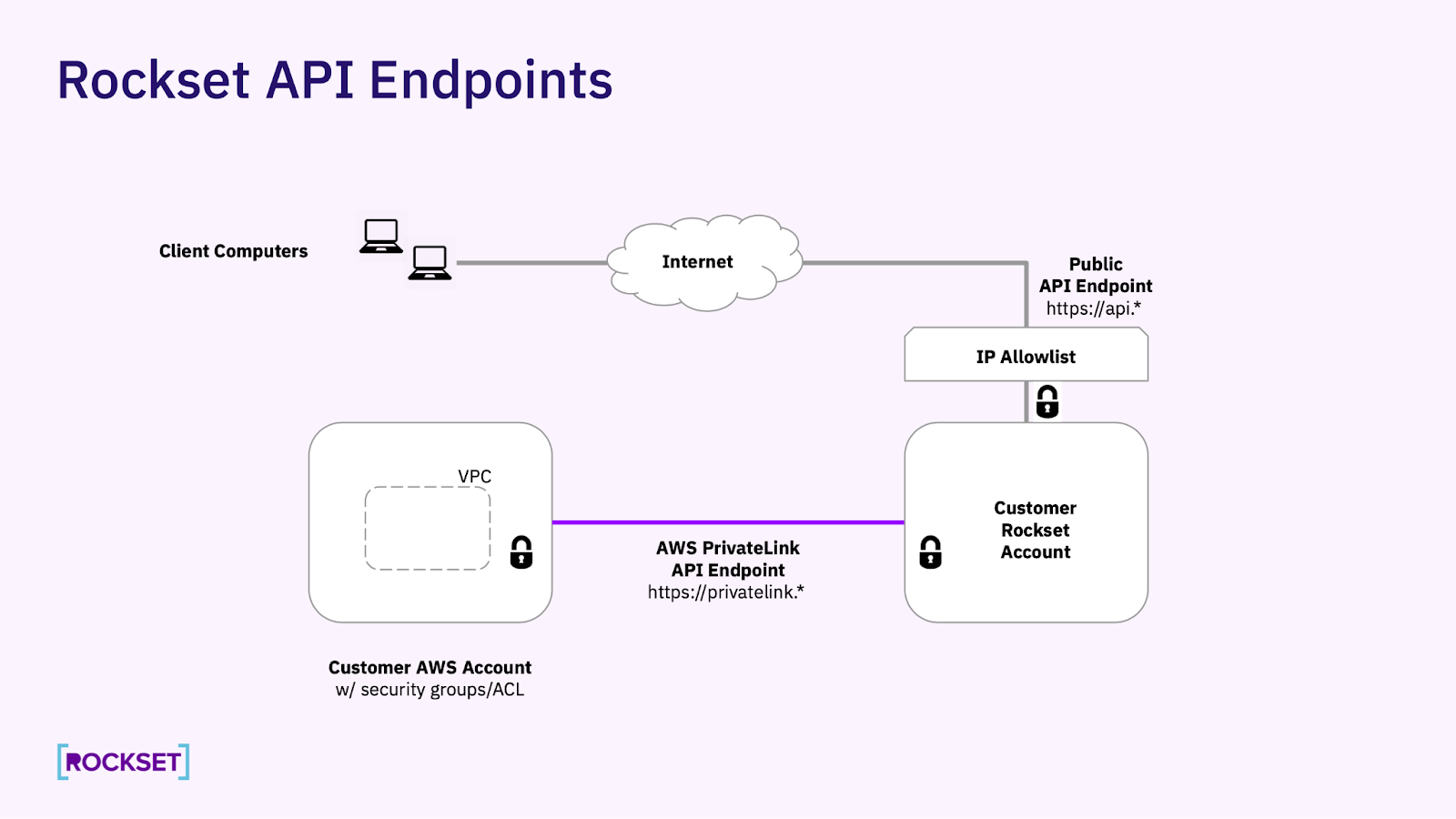
Run the following commands from any client computer that has outbound Internet connectivity in order to verify you have access to the public API endpoint. Example below uses thee public API endpoints for the Frankfurt region:
$ curl https://api.euc1a1.rockset.com/
{"message":"GO ROCKSET!"}
$ curl --request GET \
--url https://api.euc1a1.rockset.com/v1/orgs/self/users/self \
-H 'Authorization: ApiKey $ROCKSET_APIKEY'
{
"created_at": "2021-08-28T00:23:41Z",
"state": "ACTIVE",
"email": ...
}
Run the following commands from a client computer that has a connection to the network that hosts your AWS PrivateLink API endpoint in order to verify you have access to the AWS PrivateLink API endpoint. Example below uses the AWS PrivateLink API endpoint for the Frankfurt region:
$ curl https://privatelink.euc1a1.rockset.com/
{"message":"GO ROCKSET!"}
$ curl --request GET \
--url https://privatelink.euc1a1.rockset.com/v1/orgs/self/users/self \
-H 'Authorization: ApiKey $ROCKSET_APIKEY'
{
"created_at": "2021-08-28T00:23:41Z",
"state": "ACTIVE",
"email": ...
}
Step 4: Turn off the public API endpoint
Once you confirm that you are able to access your Rockset account from both privatelink and the public API endpoint, use the IP Allowlisting feature to turn off the public API endpoint. Rockset's IP Allowlisting will only affect the public API endpoint and will not have any effect on the AWS PrivateLink API endpoint.
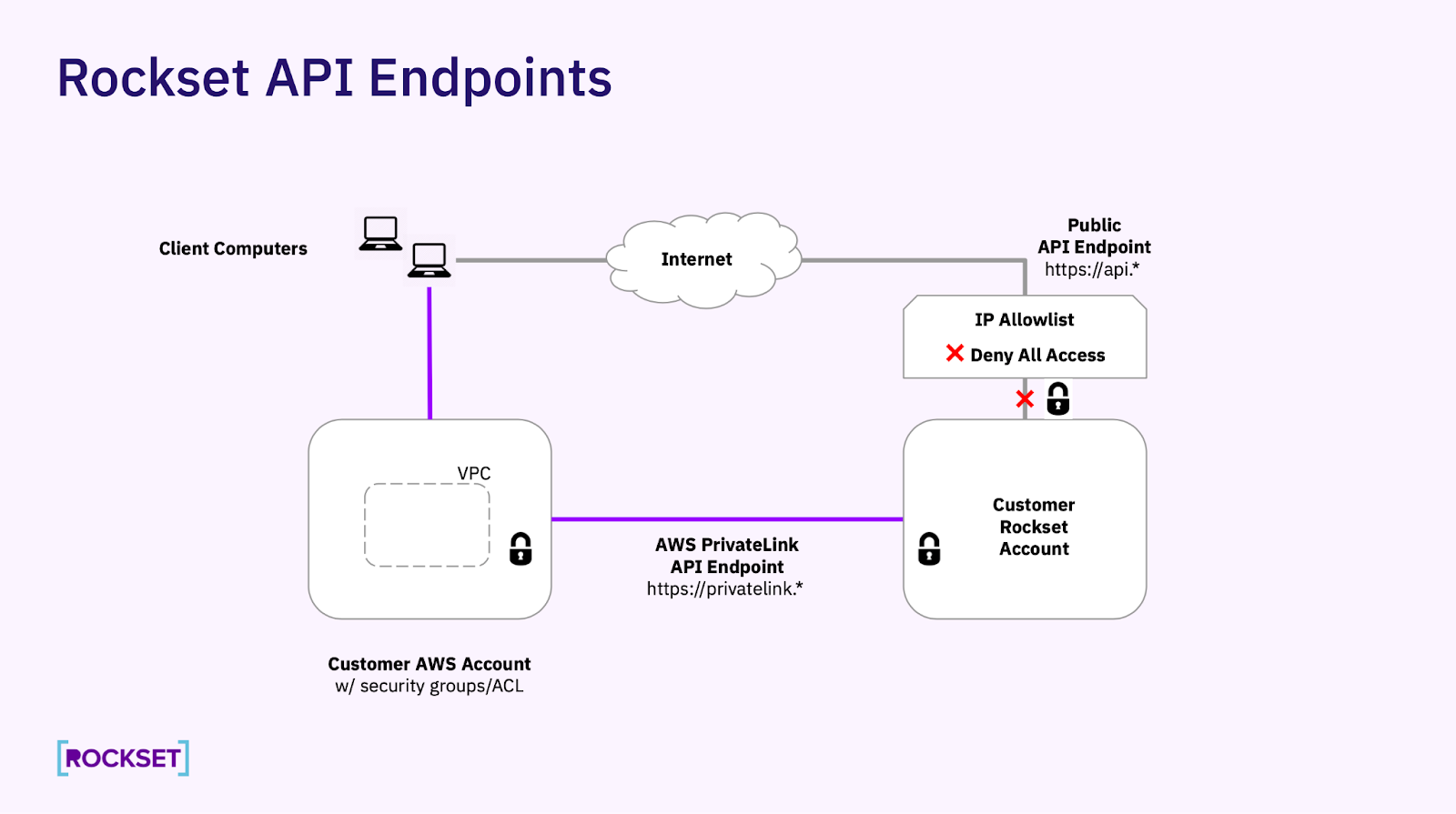
Step 5: Validate public endpoint access is blocked
Run the following commands from a client computer that has a connection to the network that hosts your AWS PrivateLink API endpoint. From there you need to verify that you have blocked access to the public API endpoint but your AWS PrivateLink API endpoint works as expected. Example for Frankfurt region:
# this should succeed
$ curl https://api.euc1a1.rockset.com/
{"message":"GO ROCKSET!"}
# this should fail
$ curl --request GET \
--url https://api.euc1a1.rockset.com/v1/orgs/self/users/self \
-H 'Authorization: ApiKey $ROCKSET_APIKEY'
{"message":"Authentication Failure","type":"AuthException", ...}
# this should succeed
$ curl --request GET \
--url https://privatelink.euc1a1.rockset.com/v1/orgs/self/users/self \
-H 'Authorization: ApiKey $ROCKSET_APIKEY'
{
"created_at": "2021-08-28T00:23:41Z",
"state": "ACTIVE",
"email": ...
}
Updated 22 days ago
